Why information security is everyone’s responsibility
This is the third in a series of blog posts from our Information Security Lead Marise Alphonso, where she talks about some of the information security issues facing the not-for-profit sector.
As we continue to embrace technology in all its forms within our workplaces, homes and lives we must remember that there is always an opportunity cost for the convenience this technology brings. Most often this cost surfaces by way of ensuring security factors are considered in how we are using technology including the interfacing processes and data.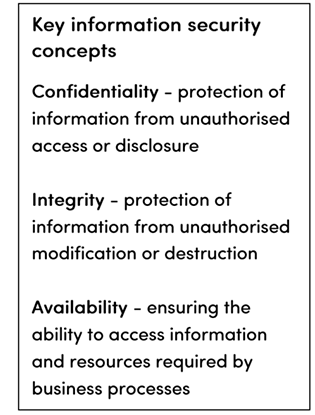
As mentioned in a previous blog post of this series, maturing security capability is not only linked to technology, but also to business processes and organisational culture. Through a security governance lens, we must ask the question "How do security practices contribute to value creation for an organisation?"
The diagram below is an indication of the majority of stakeholders for a not-for-profit organisation. Each one could be considered for the role they may play in ensuring information security-related risks that could impact on the organisation are addressed. Risk in this context could be distilled down to implementing safeguards to ensure the confidentiality, integrity and availability of organisational data and services.
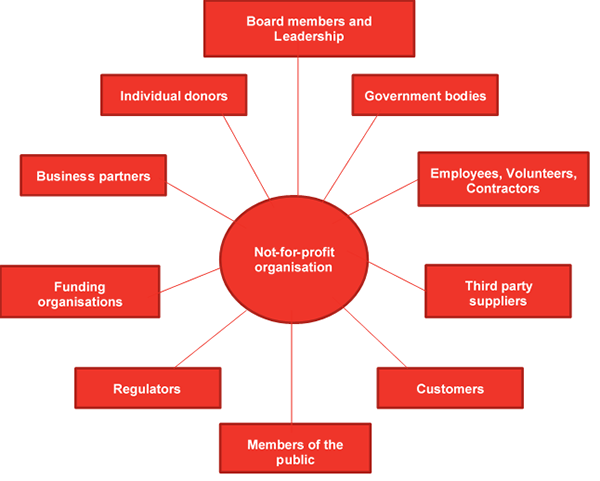
Stakeholders of a not-for-profit organisation
Responsibilities of these stakeholders focus on considerations in protecting the assets of the organisation as well as protecting the functioning of the digital economy.
A sampling of responsibilities is outlined below - there are more obligations for each stakeholder depending on the specific context and business objectives of the organisation. However, these responsibilities present the role we can all play in improving information security within our organisations, our personal lives and the broader economy.
Stakeholder |
Responsibility |
|---|---|
|
Board members and leadership |
|
|
Government bodies |
|
|
Employees, volunteers, contractors |
|
|
Third party suppliers |
|
|
Customers |
|
|
Members of the public |
|
|
Regulators |
|
| Funding organisations |
|
| Business partners |
|
| Individual donors |
|
Want to read more? Check out our other blog posts on information security.