Does your team know what phishing attacks are and how to deal with them?
During National Scams Awareness Week from 21 to 25 May, an anonymous organisation participated in a simulated phishing campaign to test staff behaviour and determine the level of vulnerability to an actual phishing attack.
The testing provider sent an email containing elements of a phishing scam to all staff in the organisation. The email claimed that the recipient’s password would expire in 72 hours and prompted them to click a link to change it.
Results showed that 14% of users clicked on the link and a further 6% entered their details on the linked page, exposing themselves and their organisation to risk. On the positive side, 10% of the users reported the email to their IT Managed Services HelpDesk.
What is phishing?
Phishing is the process of trying to gain access to sensitive information such as usernames, passwords and other personal identifiers. Scammers design phishing emails to seem authentic and official, but they contain fraudulent links or attachments asking the recipient to do something or give up sensitive information.
Example of the simulated phishing email:
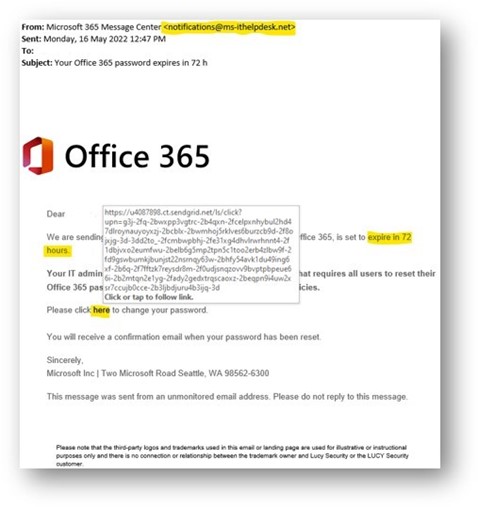
Several indicators in this email provided evidence that it was a scam:
- Suspicious-looking or unknown email address – any information regarding password changes will be conveyed through IT support teams and not from an unknown sender.
- Suspicious-looking URL – the link to reset the password had several scam indicators such as unusual web domains and excessively long URL parameters.
- The tone of the email created a sense of urgency and authority in asking the user to take specific actions.
What should staff do if they receive a phishing email?
The first step is learning to recognise phishing emails when they arrive:
- Does the email claim to be from an official source but look different or "off" in some way?
- Does the email try and create a sense of urgency to make you feel like immediate action is required?
The next step is checking the email for signs of phishing:
- Do the sender name and email address match the source the email claims to be from (e.g. does it claim to be from your organisation's IT helpdesk but comes from an external email address)?
- Sometimes a sender’s email can be imitated (what is known as email spoofing) or compromised with the email account used to send email. If an email request seems suspect, communicate with the sender via a different means e.g. via phone, to clarify they sent the email.
- Hover over any links in the email but do not click on them. Does the link lead to an unfamiliar, unusual or complicated web address?
- Does the email contain an attachment that you are not expecting? Do not open the attachment. It is best to call the sender to verify in this case.
If your staff suspect they have received a phishing email, they should:
- Notify your IT support provider.
- Report the message using their email client (this differs depending on which email client you use. For Outlook, use the "Report Message" function in the toolbar).
- Follow any instructions the IT support provider staff give them.
If your staff suspect they may have clicked a link or submitted their details to a malicious site:
- Notify your IT support provider immediately and follow their instructions.
More resources
To find out more on how you can protect your team against phishing attacks, visit the Australian Cyber Security Centre.
You can also access resources available for not-for-profits through the Digital Transformation Hub: