Using a feedback loop to strengthen security and privacy practices
This is the last in a series of blog posts from our Information Security Lead Marise Alphonso, where she talks about some of the information security issues facing the not-for-profit sector.
There has been on average 242 notifiable data breaches in Australia for the four quarters from July 2018 to June 2019, involving a range of personal information (contact details, financial information, identity and health information) disclosed to unintended parties. An earlier blog post highlighted the fact that privacy is a human right that we must endeavour to uphold by safeguarding personal information - be it our own or someone else's - entrusted to our care.
In this post, we will examine the major methods or tactics that led to these data breaches and outline some steps that could prevent similar occurrences in the future. The data points on these breaches provide us with an opportunity to utilise a feedback loop as a powerful tool for continuous improvement of cybersecurity and information security practices.
The high-level causes of the 245 data breaches reported in the period April – June 2019 are indicated in the table below, together with the methods/tactics used. Interestingly, this data mirrors what was reported in early May 2019 via the Verizon Data Breach Investigations Report where phishing and stolen credentials are top threat actions worldwide.
Cause of data breach (% of total data breaches) |
Methods or tactics used |
|---|---|
|
Malicious or criminal activity (62%)
A malicious or criminal attack deliberately crafted to exploit known vulnerabilities for financial or other gain |
|
|
Human error (34%) An unintended action by an individual directly resulting in a data breach |
|
|
System fault (4%) A business or technology process error not caused by direct human error |
|
Source: Notifiable Data Breaches Statistics Report: 1 April to 30 June 2019
Safeguards to reduce the likelihood of these methods or tactics resulting in consequential data breaches for an organisation include the following.
Malicious or criminal activity
Phishing
The image below illustrates important points of note to recognise a phishing email. Relying on technical email filters is useful, but at times malicious email can bypass these and land in user’s mailboxes. Training staff helps defend against phishing attacks. If an email is suspicious, delete it or verify first with the sender via alternate means such as via phone before taking any action.
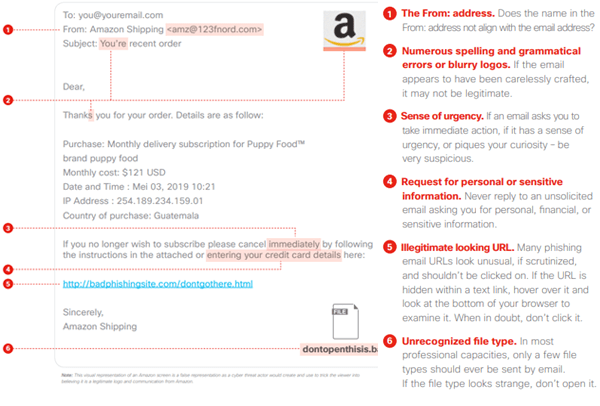
Source: CISCO Cybersecurity Series 2019 • Email Security, June 2019
Compromised or stolen credentials (unknown means)
We could speculate on how the compromised credentials are obtained. Some of the methods may be reused credentials obtained from other websites that have been breached, or use of public WiFi that has been compromised by a man-in-the-middle attack. The mitigating factors here
- Not reusing passwords across websites
- Employ multi-factor authentication where possible
- Exercise caution by not accessing sensitive information when using public WiFi
Ransomware
Ransomware can make its way into an organisation in a number of ways, for example, by users clicking on an unsuspecting link in an email and thereafter downloading software that encrypts their machines. Countermeasures include:
- Restricting IT administrative privileges on machines
- Ensuring that data is backed up regularly on media that is air-gapped
- Ensure software and systems are kept updated regularly
- Training users in the recognition of links or attachments in email that may be suspicious. If unsure, contact the sender via alternate means (e.g. phone, via their website) to confirm they have sent you the email, prior to clicking on links or downloading and opening attachments.
Human error
Unauthorised disclosure
Provide staff with privacy training on their need to understand practices for the use, disclosure, storage and access of personal information.
Loss of paperwork/data storage device
Use an incident response process to work through steps required when personal information is lost via paperwork or storage media. Where a device with sensitive information has been lost, technical protection means may be possible, such as remote wipe capability.
System faults
The measures here to reduce data breaches are more for technology providers to have practices in place to build secure software across their development lifecycles. In addition, ensuring that there are assurances provided that software within production environments has appropriate levels of security is important.
Following the above measures will assist in the reduction of data breaches from these sources. To keep up with Notable Data Breach statistics and sources of data breaches, visit the OAIC website
Want to read more? Check out our other blog posts on information security: